What is a Ring Signature?
Learn about Ring Signatures.
Ring Signatures are a way of anonymizing who authorized a particular transaction by obfuscating the legitimate sender's signature with a bunch of other public signatures. To any outside observer, it is impossible to be certain of the true sender's signature.
How does this work?
Ring signature is a type of digital signature where a group of possible signers is joined together to create a digital signature, which is essential for authorization of a transaction. The actual signer uses a one time spend key that corresponds with the output* sent from the sender's wallet. Others in this ring are decoys - signatures from similarly sized recent transaction outputs, found on the blockchain.
All of these outputs make up the input of the transaction that is being prepared by the wallet. To any external viewer, they all look equally likely to be a real input, connected to a real output. This way, the origin of the new transaction is obfuscated by making all the inputs indistinguishable and it is not possible to determine the person in the group who has created the signature. The method was initially created by Ron Rivest, Adi Shamir, and Yael Tauman in 2001, and in their paper, they proposed the White House leak dilemma [reference].
* Outputs are the resulting transaction pieces, comprising Safex Tokens, Safex Cash, and/or one of the many Advanced Transaction Outputs of the Safex Marketplace or Staking/Unstaking capability of the Safex Blockchain, and specific amount of coins heading to a destination address (and can include leftover coins being returned to the sender’s wallet as well). An input is a reference to any output from a previous transaction. Your wallet is composed of inputs (outputs that previously came IN) that you can then spend.
How to ‘’invite’’ these decoy fellas?
You, as a user, are not ‘’inviting’’ anything, you just send transactions by writing in the wallet how much you want to be sent and where. Within the Safex Wallet, by default you will have a ring size of 8. That means there will be 8 participants in that signing: you and 7 more decoys. If you want, you can lower this number by choosing your Mixin - number of decoys.
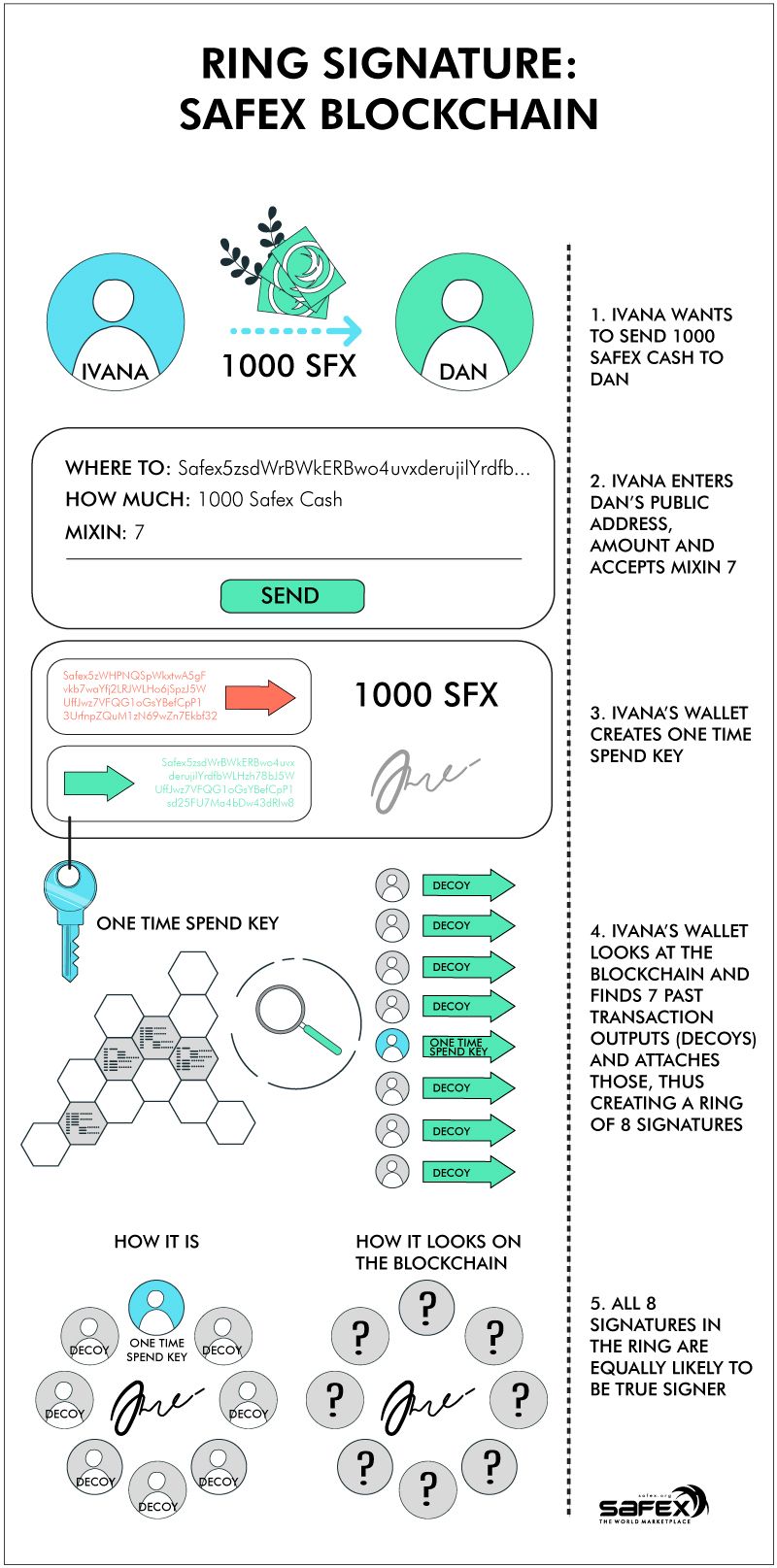
A Ring Signature within the Safex blockchain is structured as per the following simplified example:
- Ivana decides to send Dan a gift of 1000 SFX for his birthday. She enters Dan's public address in her Safex wallet, selects a mixin value of 7 and clicks the Send button.
- Ivana's wallet then creates a one-time spend key for the transaction and adds her digital signature.
- The wallet then looks at the blockchain, randomly finds 7 past transaction outputs for similarly-sized transactions and attaches those other transaction signatures, thus creating a ring of 8 signatures for the transaction (the number of extra signatures added is determined by the mixin value selected for the transaction).
- All 8 signatures in the ring are equally likely to be the true signer of the transaction, and thus, an outside observer cannot deduce the actual signer of the transaction.
- The relevant transaction inputs, along with the 8 signatures in the ring, are combined to form the transaction.
- The transaction gets processed on the blockchain, and the receiver's wallet utilizes the Private View Key to detect and decrypt the transaction.
- Ivana's signature from this transaction may also get used randomly in other future transaction mixins, thus contributing to the obfuscation of other users' transactions on the Safex network.
The above process is made possible because of techniques developed with the Diffie-Hellman key exchange.
With all the anonymity built into the transactions, it's essential to ensure that each coin output in a wallet is only spent once (to avoid double spend issues). To guarantee this, every output on the blockchain has its own unique key image, and when an output is spent, the corresponding key image is added to the list of used key images that the blockchain itself maintains. Once a key image is on the used list, that output cannot be spent a second time, thus ensuring protection from double spend issues. Further explanation of Key Images can be found here.
For a more detailed explanation on Ring Signatures, including the origins they were hypothetically created for, the reader may like to peruse this content.
