CryptoSteganography: Exploring it Further
In our Advanced Crypto Security article, the subject of CryptoSteganography was touched upon as a useful method of hiding encrypted, sensitive data in plain sight. And while a single example of using such technology was provided in that article, it’s a subject that has wide-ranging applications in the modern digital age.
Unfortunately, many of those reasons are distasteful, such as its use by terrorist groups, pedophile rings, or spies (both varieties: corporate and government) to pass on messages or stolen information. But just because there is the exploitation of the technology by those with ulterior motives, it can still be a force for good - it is beneficial for personal privacy purposes by regular people who simply want to protect their own valuable data.
This article looks to educate the reader, explore a little of the history of the technology, and finally, expand upon the possible ways in which crypto enthusiasts can apply such technology to protect not only their crypto assets but any other sensitive information they may wish to keep at hand, but out of sights, such as bank account details, or even passport information.
While cryptography is the encryption of data, and steganography is the simple concealing of data, we look to take advantage of the combined strengths of the two technologies, where the data is both encrypted AND concealed - cryptosteganography (CS).
This extra layer of protection, gained by using both technologies in combination, is fairly easy to understand: A hidden, unencrypted message isn’t necessarily secure, and a simple, encrypted file isn’t covert. But when combined, the two technologies are a formidable defense against uninvited access to your sensitive information.
Terms
Payload - the data being hidden
Carrier - the file receiving the Payload
Channel - the type of file being used as the Carrier
Embedding - the process of adding the Payload to the Carrier
Package - the new file with Payload embedded
Extraction - the process of pulling the Payload back out of the Package into its original standalone filestate.
A Brief History of Steganography
The hiding of sensitive information in plain sight is by no means a recent invention.
Historical records of its use date back to 440BC Greece, where Herodotus, in his Histories, describes how, in 499BC, Histiaeus tattooed a message onto the shaved head of a slave, allowed his hair to grow back, and the slave was sent forth as a ‘know nothing’ messenger. When the slave arrived at his destination, his head was shaved, the message was read and actioned by Aristagoras, and the Ionian Revolt was initiated. For more info on this story, head over to Histiaeus.
In more modern history, the microdots technology used by the Germans in WW2, and during the Cold War afterwards shows the technological advancements of the time, where entire photographs were able to be miniaturised to appear on paper as the dot of an i or a. Visible to the naked eye, yet invisible, so far as the information the simple dot on the page contained.
Another simple example of steganography is writing with invisible inks. This simple process is something you may recall doing as a child - writing messages on paper with lemon juice, which once dry was an invisible message, and only appeared after the heat was applied to the paper.
With the advent of the modern PC age, steganography and cryptography entered the digital realm. This has led us to this discussion, where cryptocurrency backups can be embedded into innocuous computer files, such as screensaver pictures on your Laptop, or even a favourite music file on your mobile phone, allowing us to keep the information at hand but out of sight.
Putting it into Practice
When using CS for crypto backup, there are several considerations you need to be aware of:
- The Payload data size must be smaller than the Carrier size. It is always best to use a Carrier file that is much larger than the Payload being embedded.
- If using a photograph as your Carrier:
- Use a photo you took yourself rather than one you may have found online. Then, delete the original photo after you create the Package file so that no comparison of the two files can be made in the event of your device being analysed. Remember, your goal is to safely backup your data in plain sight, undetected. If a file discrepancy can be found, you lose that element of security.
- Choose a photo with a complex scene, and avoid images that have large areas of a single colour/shade.
- If you aren’t sure your chosen CS software can be trusted, then avoid entering raw, unencrypted crypto keys or mnemonic seed data. If the Package being embedded is already itself encrypted (e.g., A wallet .keys file), then the risk of using software of unknown origins is lessened.
- Using an offline or air-gapped PC/laptop to create these Package files would allow you to feel safer hiding raw data (e.g., keys/mnemonic seed text files), so long as the same security practices were subsequently employed if you later need to access the Payload data.
- Software that has the source code available for inspection, such as the Steghide software used in this and the previous article, allows users to inspect the code and be confident there is no malicious script that would send your sensitive data back to the software author or elsewhere. As Steghide has been in use since 2002/3, it has also undergone many years of scrutiny by previous users and is a well-respected CS program, leading to increased confidence in the integrity of the code. Those with the requisite skill set can also build their binaries from the raw code for additional peace of mind and/or fork and modify the software for their own purposes.
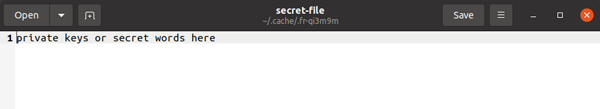
- If you do prefer to embed your private keys or mnemonic seed into the image, then you have the choice of raw data (for some programs, but not Steghide) or as a text file, which you may or may not have already encrypted. The more secure method would be to prepare the information into a text file and encrypt it separately prior to the embedding process. Of course, for every level of encryption you add, you need to subsequently remember the passphrases to decrypt it.
- Encryption of the Payload is only as strong as the length of your passphrase. The longer it is, the more secure. The author personally aims for (and recommends) 21+ characters for all crypto-related passphrases, ideally with a combination of upper and lower case letters, numbers, and special characters.
Command-line examples using the Steghide software
Once you settle on a CS program you feel comfortable with, be sure to check all functionality of the software works. Don’t simply embed a Payload and then assume it will extract when your needs call upon it. Test the extraction process to ensure you have an understanding of the full process so that, in a worst-case scenario, you can indeed access your encrypted backups.
- Embed
Text file in an audio file
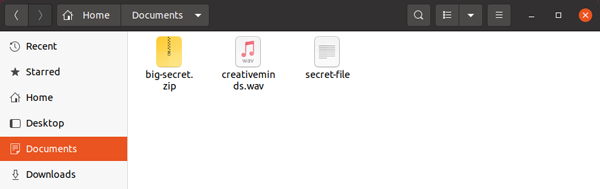
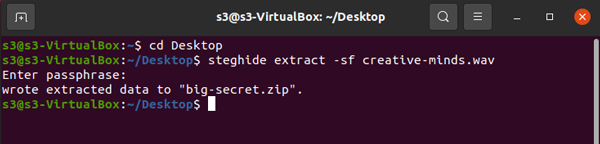
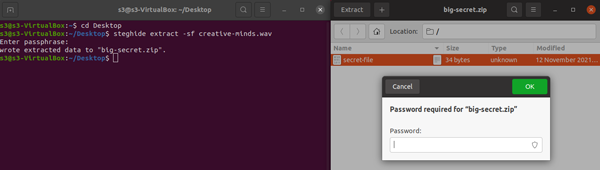
In the above, the secret-file has been encrypted into the big-secret.zip embed-in-wav.
The encrypted .zip file is then embedded into the .wav file.
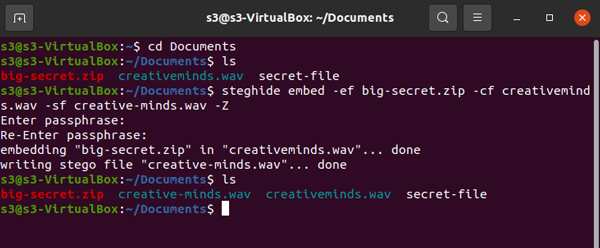
Initial .wav file
Initial file
Original .mp3 sourced from Music: www.bensound.com
https://www.bensound.com/royalty-free-music/track/creative-minds and converted to .wav for the purposes of this CS demostration.
(Steghide is unable to work with.mp3 files, hence the file conversion)
After .zip file embedded
With the payload file safely and securely embedded into the carrier file, the resulting Package file is the identical file size.

The new file can be transferred elsewhere, just like any other file, and the integrity of the file will remain unchanged. You could safely keep a copy in the cloud (Google drive, Dropbox, etc) or even send a copy to your Protonmail email account.
- Check if an image has a Package embedded.
steghide info -sf filename
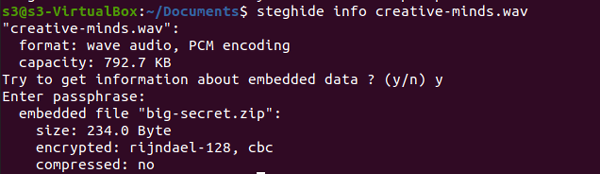
- Extract
steghide extract -sf filename
For those who may prefer to learn-by-doing, feel free to download the files above and have a play.
- The steghide password to extract the zip file from the .wav file is: safex
- The archive password to extract the .txt file from the .zip file is: passphrase
Steghide official documentation.
Note: The author has been unable to get the Windows version of Steghide to run on a Win10 laptop, so has only used the Ubuntu version.
While the author is comfortable using the Steghide software, readers should find software they themselves feel comfortable and confident using - there are many CS software choices available online.
Other technology applications
- Proving ownership/authorship: Embedding dates, watermarks, serial numbers, or other copyright information within an image, sound, or video file.
- Identifying sources of corporate/political/government information leaks:
- Each employee is sent the same Carrier file. Still, each gets a different Payload embedded, allowing the overarching entity to identify the source later, once it becomes public or appears elsewhere.
- Travellers wanting to keep access to their passport photo and info but not have it visibly displayed on their laptop files can embed the passport pages photo in another photo.
- Proving ownership/authorship: Embedding dates, watermarks, serial numbers, or other copyright information within an image, sound, or video file.
Identifying sources of corporate/political/government information leaks:- Each employee is sent the same Carrier file. Still, each gets a different Payload embedded, allowing the overarching entity to identify the source later, once it becomes public or appears elsewhere.
- Travellers wanting to keep access to their passport photo and info but not have it visibly displayed on their laptop files can embed the passport pages photo in another photo.
Potential issues: crypto asset estate management
A significant drawback to using CS as part of your crypto asset estate management is that, in the event of your death, the beneficiary to your estate will need to know the exact software program you used to create the Package, as the same software will be required to decode the Payload.
It may be better to only use CS for your own personal data backup purposes and use something like Shamir’s Secret Sharing Scheme for crypto-asset estate management, as previously discussed in the earlier article.
Further Reading
There are much broader applications of this technology, so if the reader is interested in this topic, some of these links may prove interesting:
Steganography
Code Wars: Steganography, Signals Intelligence, and Terrorism
Microdots
Best Tools to Perform Steganography
Information Hiding - A Survey
Additionally, both government and law enforcement have a wealth of information and techniques on the detection of embedded data, which many of the above links also delve into.
