Advanced Crypto Security Tips
Read about Advanced Crypto Security, use the tips we are presenting, and keep your Safex and other coins adequately backed up and safe.
This article will expand upon the simple crypto-security practices outlined in this text and give you a few ideas for improving your security and crypto backup processes.
So, you may have put a few thousand dollars into assorted crypto projects and made backups in the form of paper wallets and files on USB drives that contain Private Keys, Mnemonic Seeds, and maybe your wallet software files. You feel you have taken the necessary precautions for the value of the investment.
But what happens if one or more of your coins does a 1000X and you're suddenly sitting on a small fortune? Are your backup practices still sufficient? What if you need to travel overseas and want to access your crypto wallets? What if, heaven forbid, your house burns down… will your existing backup practices allow you to recover your crypto?
Several advanced ideas are outlined below as options to improve the level of security for your crypto and backup processes. This isn't an exhaustive list by any means - indeed, you may already have advanced processes in place that you feel are sufficient. But, if you haven't really thought about it much (or perhaps you've identified you could improve your crypto/backup security and have been procrastinating), hopefully, this article provides the impetus for you to take those next steps and upgrade the security on your crypto backups.
There are three basic situational security considerations for your crypto backups:
- Security At Home
- Third-Party Secure Storage Facilities
- Security When Travelling
Security At Home
This is the starting point for everyone.
While minimum requirements can be as simple as a piece of paper hidden somewhere, crypto users should be considering a 2-hr Fire Retardant Safe, containing paper wallets and several USB drives containing text files of Private Keys and Mnemonic Seeds, as the basic precaution against crypto loss.
Not all safes are built to the same standard. In the event of a house fire, you want some peace of mind that your precious documents and other treasures will remain unharmed. A house fire rarely lasts more than 2 hours because it gets extinguished or the house has burnt to the ground in less time. A 2-hour fire retardant safe is engineered to withstand that level of heat and protect its contents from harm.
However, best practice dictates that you should have some additional redundancy. An extra backup copy in a different location.
Third-Party Secure Storage Facilities
This can be a bank security box, another safe owned by a friend or family member, your lawyer, or even a corporate, private security storage facility.
Keeping your crypto backups at a third-party location requires some additional considerations, the most obvious being: how to ensure the information isn't accessible by the third party custodian, or any other person who may gain physical access to your backup by legal (eg. warrant) or illegal (eg. burglar) means. [This should also be a consideration for your home safe.]
Security When Traveling
So you need/want to travel abroad and retain access to your crypto, maybe to pay bills, day trade, or in the case of the Safex Marketplace, buy goods and services wherever you may be.
With many countries now implementing customs regulations that allow border control officers to demand passwords for electronic devices upon entry to the country, how can you safely travel with your crypto and not become vulnerable to losing control of your precious crypto information?
The following advanced security practices can be of assistance in one or more of the above situations.
Encrypted USB Drives

Starting at about 20x the price of regular USB drives, an encrypted USB drive is a huge step forward in protecting your crypto backups and software wallet files.
This particular model pictured above has full-disk military-grade XTS-AES 256-bit hardware-based encryption and only allows ten consecutive wrong codes before it simply wipes all data on the drive and resets itself. If an unwanted third party were to gain physical possession of the USB drive, they would have to be exceedingly lucky to unlock it in ten attempts, considering you can use a 7-15 digit PIN. (Even at the minimum seven-digit PIN, that is 10 million possible combinations: 0000000 - 9999999.)
Once the encryption PIN has been set, you can safely store this USB drive with any third party. Remember to save your PIN in a safe place. If you lose or forget your PIN, there is NO way to access the data stored. A memorable word is often easier to remember, and the keypad on this model also includes letters for just such a purpose.
In your own home, you can also keep an encrypted USB drive such as this conveniently handy to use and not have a fear of the information being accessed by an intruder.
Additionally, you can use it while traveling with your laptop to store your crypto-related files and information and only unlock it when you are in a safe location, all the while knowing that in an emergency, you can simply remove the USB drive from the laptop and it instantly locks.
Another feature of this model is Read Only mode, allowing a user to write their private keys and mnemonic seed document/s to the USB drive, then set it to Read Only, to avoid any further changes being made to the data.
Crypto Steels
So we've talked about fire retardant safes, but what about a worst-case scenario, where the papers and USB drives in the safe get destroyed in a fire. What else could you have done to ensure you retain handy access to your important crypto wallet/s?
The answer is steel, ideally stainless steel: waterproof, fireproof... Virtually damage-proof.
Whilst commercial crypto-steel products are available for sale, they're a single-purpose product, and if you can only buy them online, then you're basically giving your address to a stranger and telling them you're serious about crypto.
For a more private option, simply buy a strip of stainless steel and a letter punch kit from any hardware store. Then punch your mnemonic seed phrase into the metal strip.

There are various ways of doing this:
- If you want to keep the information in your safe, you may need several short steel strips, which each contain part of your seed phrase. In this case, you thread them together onto a key ring by drilling a hole at one end of each strip.
- An alternative is to put all the words onto a single long strip and then hide the seed phrase in 'plain sight' by screwing it under a floorboard or in the ceiling cavity, etc.
Laptop tweaks for traveling with crypto
OPSEC - OPerational SECurity - should be a high priority for any crypto user, particularly if you plan on traveling and want to access your crypto whilst abroad. Some laptop preparations before departure would be highly recommended.
Importantly, don't ever keep Private Keys or Mnemonic Seed phrases on your laptop in an unencrypted form. Don't have shortcuts to crypto-related websites or wallet software on your desktop, where any passer-by could see over your shoulder. Additionally, only access your crypto when you are in a private, secure location - not in a public space.
An even more secure option is to have your laptop configured in dual boot mode or have a virtual machine (VM) installed, where you only access your crypto-related stuff in the non-default boot mode or only within the VM environment. In this way, if your laptop falls into the wrong hands, any casual exploration of your laptop files and folders would show no crypto-related information.
As with accessing fiat banking, you should always be cautious when using a third-party wifi connection. A VPN account is a great way to help ensure you aren't transmitting any sensitive data that an intermediary network gateway could intercept.
For Safex, as an example, you could run Windows as your default boot OS and Ubuntu 20 as the dual boot option. Within Ubuntu, you could have a local node and TWM Wallet installed, where you start the node and let it sync, and then start the TWM wallet software. Then, you connect to the local node when you open the wallet files stored on your encrypted USB travel drive - a self-contained, crypto environment with high security and very low outward visibility. Depending on the ports available with your VPN service, you could also do all of this process within the VPN environment.
Taking your backup security further with Shamir’s Secret Sharing Scheme
With the previously described backup and security protocols in place, a crypto user is well-positioned to ensure they never lose access to their precious Keys/Seeds and can safely access their crypto whilst traveling, without necessarily drawing any attention to themselves. But have you, the reader, given any thought to what would happen to your crypto in the event of your death?
Whilst it isn't really something we like to think about, having a system in place that allows your crypto assets to be passed on to your next of kin or other chosen beneficiaries will ensure it doesn't just become 'lost crypto'.
However, you can't simply go writing your Keys/Seed into your Will, as it would leave your crypto assets immediately vulnerable.
But now that you have an encrypted USB Drive holding your keys/seed (or a set of crypto steels hidden somewhere), you can use Shamir's Secret Sharing Scheme (SSSS) to create a secure set of clues that would allow your crypto assets to be passed on in the event of your eventual demise.
If you aren't familiar with SSSS, then a quick read of this text is recommended.
So, how can you use SSSS to safely give future access to your crypto keys without doing so earlier than you intend?
Consider the following scenario:
- Your Will is held by your lawyer (1).
- You have an encrypted USB Drive containing your Keys/Seed lodged in a security box at your bank (2).
- You have two beneficiaries who you would like to have a share of your crypto after your passing (3,4).
- You have a trusted friend nominated as the Executor of your Will (5).
- You have a safe at home, and your bank security box contains an envelope with the combination and a spare key (6).
Using SSSS, we can create a set of Shares that would allow the encrypted USB Drive PIN to be reconstructed.
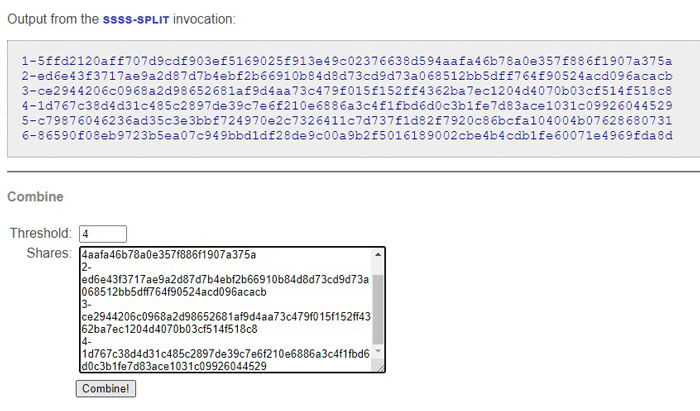
You could have an SSSS with 6 Shares (one in your safe, one in the bank security box with the USB Drive, and one each held by your lawyer, beneficiaries, and Executor). The other thing you would need to decide upon is the Threshold - how many of the Shares need to be brought together to reconstruct the PIN for the USB Drive.
Requiring all 6 Shares as the Threshold for reconstruction is problematic - what if a Share can't be found? In this scenario, you could set a Threshold of 4 Shares and be confident that your crypto wouldn't be lost whilst still not allowing premature access to it.
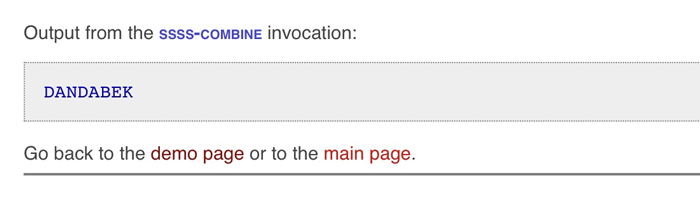
In this imaginary scenario, the PIN for the encrypted USB Drive in the bank security box is: DANDABEK
On the demo page of the above website, you can enter the number of Shares, the Threshold, and the PIN into the respective fields.
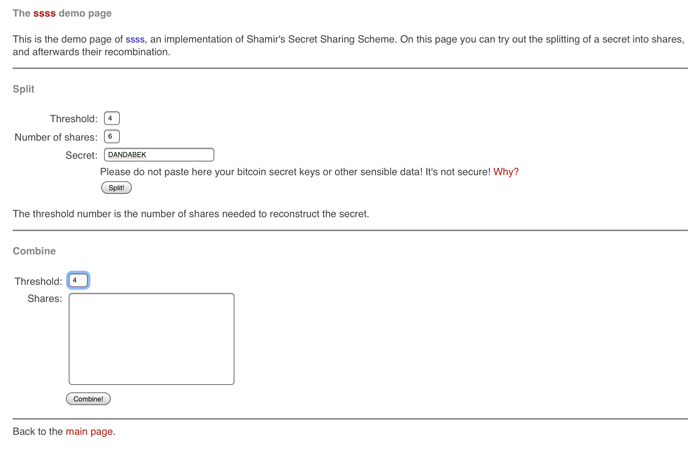
Hit the Split button and it will generate the Shares:
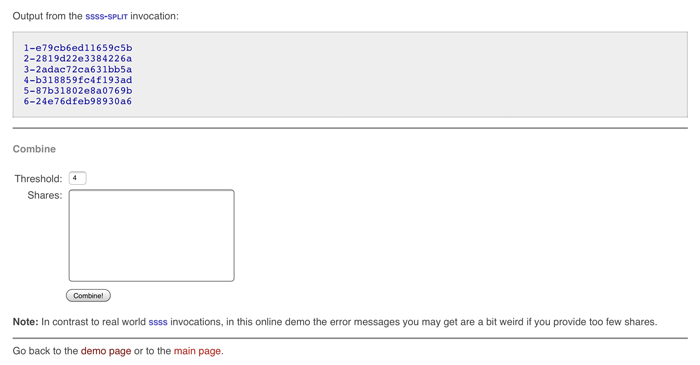
1-e79cb6ed11659c5b
2-2819d22e3384226a
3-2adac72ca631bb5a
4-b318859fc4f193ad
5-87b31802e8a0769b
6-24e76dfeb98930a6
Each of those Shares can then be disseminated on pieces of paper (or steel strips) to the people/locations in the scenario. As the Threshold was set to 4, any four of them in combination will regenerate the PIN for the Encrypted USB Drive in your bank security box.
Feel free to enter any four of the above shares into the Combine section of the demo website and see the DANDABEK PIN recreated.
Example:
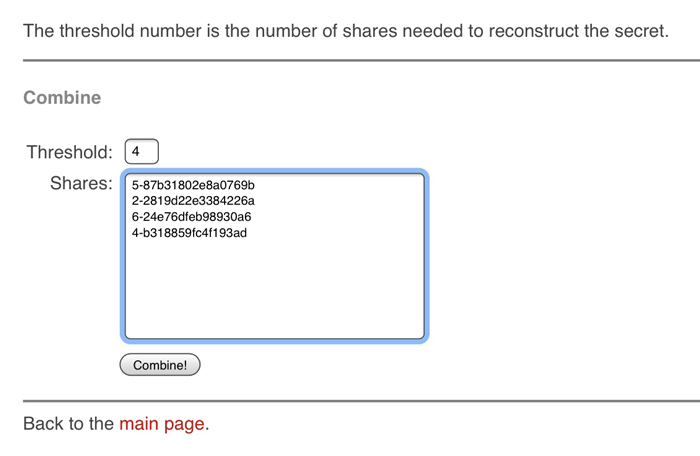
Given the scenario parameters, it would be practically impossible to bring 4 shares together AND gain access to the USB Drive in the bank security box BEFORE your death. If you wanted to guarantee that at least one of your beneficiaries in the above scenario used their Share, you would set the Threshold to 5, instead of 4.
But this is just an example for you to consider. Each of us has our own particular requirements when it comes to crypto estate management, so find a system that works for you. You could just as easily use SSSS to reveal the location of your hidden crypto steels.
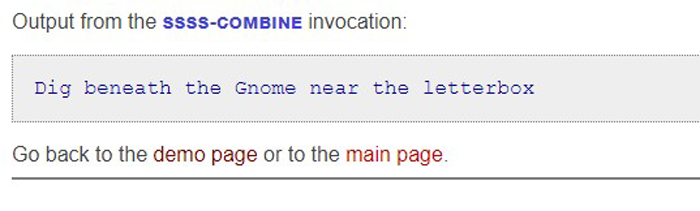
It is important to have a system in place and not keep putting it into the too-hard basket.
CryptoSteganography
Perhaps you're traveling, and your encrypted USB Drive becomes corrupted, is lost/stolen, or you intentionally wipe it due to circumstances you find yourself in. You don't necessarily want to be stuck overseas without access to your crypto, so have a backup plan or two - some redundant access to your keys, seed, or wallet files.
An extra way of protecting sensitive data is to hide it in plain sight. Steganography embeds data into a computer file, usually an image or audio file - security through obscurity - without encryption.
Taken to the next level, CryptoSteganography is the embedding of encrypted data into a file.
Let's say you have an image you want to use for your laptop wallpaper:

Using CryptoSteganography, you can embed an encrypted copy of your Mnemonic Seed phrase, Private Keys, or even your Safex wallet .keys file, into the image. So long as you remember the passphrase for the encrypted image, you can subsequently extract your embedded data in an emergency situation.
You can educate yourself on the embedding and extracting processes here. Unfortunately, the Linux package referenced in that article refused to work for me due to missing/incompatible package versions, which I wasn't able to rectify.
Instead, the steghide package was found to work correctly, as referenced here. It is only encrypted to AES128 by default, whereas the non-functional package was encrypted in AES256, had it worked.
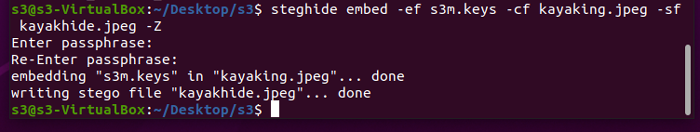
So, let's say we have our Safex wallet .keys file, and we want to embed it in the above image of kayaks on the lake.
We run the steghide command-line instruction to create the new image with the AES-128 encrypted data embedded therein. In this example, an old Stagenet wallet .keys file was embedded. Important: use a strong passphrase you will remember!
As you can see in compared kayak photos above, there's no visible difference to the naked eye between the two images. As you're the only person who knows there's a hidden packet of information in the image, you simply treat it as 'just another image'. Set it as your desktop wallpaper, so there's no mystery about why you'd have the image on your PC.
In the event you need to access the Safex .keys file, you run the extraction command against the image, enter your passphrase, and voila - your file will be saved as the output result.
Each user will undoubtedly have their own preference as to what security protocols they feel the need to implement. This article simply looks to raise awareness of possible shortcomings in readers' current crypto security measures and hopefully offers some insight into additional measures that can be taken to help avoid the loss of crypto by happenstance.
